Instalacija Davaoca Identiteta (Shibboleth IdP 4.3.1) - Debian/Ubuntu
Priprema pred instalaciju¶
Podesiti IP TABLES¶
Najpre je potrebno instalirati iptables softverski paket i izvršiti početna podešavanja ukoliko već niste.
Otvoriti portove 80 (HTTP) i 443 (HTTPS)
To se može uraditi na sledeći način:
Otvoriti port 80 i 443 dodavanjem sledećih linija u fajl:
-A INPUT -s xxx.xxx.xxx.xxx/255.255.255.xxx -p tcp -m tcp --dport 80 -j ACCEPT
-A INPUT -s xxx.xxx.xxx.xxx/255.255.255.xxx -p tcp -m tcp --dport 443 -j ACCEPT
Napomena: Navedene linije je potrebno uneti bavezno iznad linije: -A INPUT -j REJECT --reject-with icmp-host-prohibited
Sačuvati izmene:
Podesiti hosta¶
U okviru čitavog uputstva smatraće se da je domen VM idp.institucija.ac.rs, tako da na svim mestima umesto ovog naziva domena potrebno je da unesete naziv po vašem izboru.
Veoma je važno da FQDN (Full Qualified Domain Name) i pun hostname (# hostname -f) ove VM, npr. idp.institucija.ac.rs, koji se podešava u okviru ove sekcije bude isti kao i domen koji je adekvatno podešen na DNS serveru, a taj domen će se takođe kasnije koristiti za kreiranje sertifikata.
Podešavanje host podataka
Dat je primer postavljanja idp.institucija.ac.rs kao FQDN podatka, koji je potrebno zameniti FQDN podatkom Vašeg Davaoca Identiteta, kao i postavljanja HOSTNAME podatka: idp, koji je potrebno zameniti hostname podatkom Vašeg Davaoca Identiteta.
Na kraju fajla se unosi linija u formi: IP ADRESA FQDN HOSTNAME Npr:
Postaviti hostname
Koristi se komanda sledeće forme: hostnamectl set-hostname HOSTNAME
Hardverski zahtevi¶
Hardverski zahtevi:
- CPU: 2 Core (64 bit)
- RAM: 4 GB
- HDD: 20 GB
- OS: Debian 10 / Ubuntu 18.04 / Ubuntu 20.04 / Ubuntu 22.04
Softver koji će biti instaliran¶
Softver koji će biti instaliran:
- ca-certificates
- ntp
- vim
- Amazon Corretto 11 JDK
- jetty 9.4.x
- apache2 (>= 2.4)
- openssl
- gnupg
- libservlet3.1-java
- liblogback-java
Instalirati potrebne pakete:
apt install vim wget gnupg ca-certificates openssl apache2 ntp libservlet3.1-java liblogback-java -y --no-install-recommends
Instalirati Amazon Corretto JDK:
Provera verzije instaliranog Java paketa:
Provera da li Java funkcioniše:
Postaviti varijablu JAVA_HOME:
Instalacija Davaoca Identiteta ( Shibboleth IdP 4.3.1 )¶
Preuzeti i otpakovati Shibboleth Identity Provider v4.3.1 repozitorijum na lokaciji /usr/local/src:
wget https://shibboleth.net/downloads/identity-provider/latest4/shibboleth-identity-provider-4.3.1.tar.gz
Pokrenuti skriptu za instalaciju:
U procesu instalacije biće ispisana sledeća obaveštenja i biće postavljena pitanja.
Kada se prikažu određene linije koje su markirane bojom u nastavku potrebno je uneti odgovarajuće podatke:
- Source (Distribution) Directory (press to accept default): [/usr/local/src/shibboleth-identity-provider-4.3.1] ? Klik ENTER
- Installation Directory: [/opt/shibboleth-idp] ? Klik ENTER
- Backchannel PKCS12 Password: ###LOZINKA-ZA-BACKCHANNEL###
- Re-enter password: ###LOZINKA-ZA-BACKCHANNEL###
- Cookie Encryption Key Password: ###LOZINKA-ZA-BACKCHANNEL###
- Re-enter password: ###LOZINKA-ZA-BACKCHANNEL###
- SAML EntityID: [https://idp.institucija.ac.rs/idp/shibboleth] ? Klik ENTER
- Attribute Scope: [institucija.ac.rs] ? Klik ENTER
Objašnjenje za :
- Backchannel PKCS12 Password: predstavlja lozinku za Backchannel
- Cookie Encryption Key Password: predstavlja lozinku za enkripciju kolačića
- Attribute Scope: Scope treba da bude validan domen institucije
Napomena:
Od ovog momenta, promenljiva idp.home odnosi se na direktorijum: /opt/shibboleth-idp
Napravite rezervnu kopiju lozinke ###LOZINKA-ZA-BACKCHANNEL### negde ukoliko Vam zatreba u budućnosti.
Lozinka ###LOZINKA-ZA-COOKIE-ENCRYPTION### će biti sačuvana u fajlu /opt/shibboleth-idp/credentials/secrets.properties kao idp.sealer.storePassword i idp.sealer.keyPassword vrednost.
Buildfile: /usr/local/src/shibboleth-identity-provider-4.3.1/bin/build.xml
install:
Source (Distribution) Directory (press to accept default): [/usr/local/src/shibboleth-identity-provider-4.3.1] ? Klik Enter
Installation Directory: [/opt/shibboleth-idp] ? Klik Enter
INFO [net.shibboleth.idp.installer.V4Install:158] - New Install. Version: 4.3.1
INFO [net.shibboleth.idp.installer.V4Install:601] - Creating idp-signing, CN = idp.institucija.ac.rs URI = https://idp.institucija.ac.rs/idp/shibboleth, keySize=3072
INFO [net.shibboleth.idp.installer.V4Install:601] - Creating idp-encryption, CN = idp.institucija.ac.rs URI = https://idp.institucija.ac.rs/idp/shibboleth, keySize=3072
Backchannel PKCS12 Password: ###LOZINKA-ZA-BACKCHANNEL###
Re-enter password: ###LOZINKA-ZA-BACKCHANNEL###
INFO [net.shibboleth.idp.installer.V4Install:644] - Creating backchannel keystore, CN = idp.institucija.ac.rs URI = https://idp.institucija.ac.rs/idp/shibboleth, keySize=3072
Cookie Encryption Key Password: ###LOZINKA-ZA-COOKIE-ENCRYPTION###
Re-enter password: ###LOZINKA-ZA-COOKIE-ENCRYPTION###
INFO [net.shibboleth.idp.installer.V4Install:685] - Creating backchannel keystore, CN = idp.institucija.ac.rs URI = https://idp.institucija.ac.rs/idp/shibboleth, keySize=3072
INFO [net.shibboleth.utilities.java.support.security.BasicKeystoreKeyStrategyTool:166] - No existing versioning property, initializing...
SAML EntityID: [https://idp.institucija.ac.rs/idp/shibboleth] ? Klik ENTER
Attribute Scope: [institucija.ac.rs] ? Klik ENTER
INFO [net.shibboleth.idp.installer.V4Install:474] - Creating Metadata to /opt/shibboleth-idp/metadata/idp-metadata.xml
INFO [net.shibboleth.idp.installer.BuildWar:103] - Rebuilding /opt/shibboleth-idp/war/idp.war, Version 4.3.1
INFO [net.shibboleth.idp.installer.BuildWar:113] - Initial populate from /opt/shibboleth-idp/dist/webapp to /opt/shibboleth-idp/webpapp.tmp
INFO [net.shibboleth.idp.installer.BuildWar:92] - Overlay from /opt/shibboleth-idp/edit-webapp to /opt/shibboleth-idp/webpapp.tmp
INFO [net.shibboleth.idp.installer.BuildWar:125] - Creating war file /opt/shibboleth-idp/war/idp.war
BUILD SUCCESSFUL
Total time: 1 minute 19 seconds
Instalacija Jetty 9 Web Servera¶
wget https://repo1.maven.org/maven2/org/eclipse/jetty/jetty-distribution/9.4.43.v20210629/jetty-distribution-9.4.43.v20210629.tar.gz
Kreirati jetty-src folder kao simbolički link. Ovo će biti korisno za ažuriranje Jetty softvera u budućnosti:
Kreirati jetty korisnika i grupu:
Podesiti Jetty konfiguraciju koja će da pregazi default-u i koja će da podnese prolazak update-a:
Podesiti Jetty konfiguraciju koja će da pregazi inicijalnu i koja će da podnese ažuriranje:
Kreirati /opt/jetty/tmp direktorijum tako da se koristi od strane Jetty softvera:
Kreirati Jetty Log direktorijume:
Preuzeti fajl jetty:
Omogućiti da jetty servis može da se učitava iz komandne linije (loadable):
Proveriti da li je jetty ispravno podešen:
Provera statusa jetty procesa:
Jetty NOT running
JAVA = /usr/bin/java
JAVA_OPTIONS = -Djetty.home=/usr/local/src/jetty-src -Djetty.base=/opt/jetty -Djava.io.tmpdir=/opt/jetty/tmp
JETTY_HOME = /usr/local/src/jetty-src
JETTY_BASE = /opt/jetty
START_D = /opt/jetty/start.d
START_INI = /opt/jetty/start.ini
JETTY_START = /usr/local/src/jetty-src/start.jar
JETTY_CONF = /usr/local/src/jetty-src/etc/jetty.conf
JETTY_ARGS = jetty.state=/opt/jetty/jetty.state jetty-started.xml
JETTY_RUN = /var/run/jetty
JETTY_PID = /var/run/jetty/jetty.pid
JETTY_START_LOG = /var/log/jetty/start.log
JETTY_STATE = /opt/jetty/jetty.state
JETTY_START_TIMEOUT = 60
RUN_CMD = /usr/bin/java -Djetty.home=/usr/local/src/jetty-src -Djetty.base=/opt/jetty -Djava.io.tmpdir=/opt/jetty/tmp -jar /usr/local/src/jetty-src/start.jar jetty.state=/opt/jetty/jetty.state jetty-started.xml
Pokrenuti Jetty proces:
Ponovna provera statusa jetty procesa:
Provera statusa jetty procesa:
Jetty running pid=3886
JAVA = /usr/bin/java
JAVA_OPTIONS = -Djetty.home=/usr/local/src/jetty-src -Djetty.base=/opt/jetty -Djava.io.tmpdir=/opt/jetty/tmp
JETTY_HOME = /usr/local/src/jetty-src
JETTY_BASE = /opt/jetty
START_D = /opt/jetty/start.d
START_INI = /opt/jetty/start.ini
JETTY_START = /usr/local/src/jetty-src/start.jar
JETTY_CONF = /usr/local/src/jetty-src/etc/jetty.conf
JETTY_ARGS = jetty.state=/opt/jetty/jetty.state jetty-started.xml
JETTY_RUN = /var/run/jetty
JETTY_PID = /var/run/jetty/jetty.pid
JETTY_START_LOG = /var/log/jetty/start.log
JETTY_STATE = /opt/jetty/jetty.state
JETTY_START_TIMEOUT = 60
RUN_CMD = /usr/bin/java -Djetty.home=/usr/local/src/jetty-src -Djetty.base=/opt/jetty -Djava.io.tmpdir=/opt/jetty/tmp -jar /usr/local/src/jetty-src/start.jar jetty.state=/opt/jetty/jetty.state jetty-started.xml
Konfiguracija Jetty 9 Web Servera¶
Konfigurisati IdP Context Descriptor. Kreirati direktorijum /opt/jetty/webapps:
Preuzeti fajl idp.xml:
Postaviti da vlasnik glavnih direktorijuma Davaoca Identiteta bude jetty:
Pregled direktorijuma /opt/shibboleth-idp:
root@idp:/opt/shibboleth-idp# ls -l
total 48
drwxr-xr-x 3 root root 4096 Aug 16 10:46 bin
drwxr-xr-x 8 jetty root 4096 Aug 16 10:46 conf
drwxr-xr-x 2 jetty root 4096 Aug 16 10:46 credentials
drwxr-xr-x 7 root root 4096 Aug 16 10:46 dist
drwxr-xr-x 2 root root 4096 Aug 16 10:46 doc
drwxr-xr-x 5 root root 4096 Aug 16 10:46 edit-webapp
drwxr-xr-x 4 root root 4096 Aug 16 10:46 flows
drwxr-xr-x 2 jetty root 4096 Aug 16 10:46 logs
drwxr-xr-x 2 root root 4096 Aug 16 10:46 messages
drwxr-xr-x 2 jetty root 4096 Aug 16 10:46 metadata
drwxr-xr-x 4 root root 4096 Aug 16 10:46 views
drwxr-xr-x 2 jetty root 4096 Aug 16 10:46 war
Restartovati Jetty servis:
SSL konfiguracija - Apache2 (front-end Jetty)¶
Kreirati DocumentRoot:
wget https://docs.amres.ac.rs/download/shibboleth/debian/000-idp.institucija.ac.rs.conf -O /etc/apache2/sites-available/$(hostname -f).conf
Fajl /etc/apache2/sites-available/$(hostname -f).conf je potrebno izmeniti. Uneti nazive sertifikata i ključa i podatke o serveru.
Fajl /etc/apache2/sites-available/000-$(hostname -f).conf sa svim potrebnim izmenama:
Komercijalni SSL sertifikat¶
Kreiranje komercijalnog SSL sertifikata i ključa:
Komercijalni sertifikat i ključ treba da budu vrste GÉANT OV SSL kog kreirate po uputstvu:
- HTTPS Server Certificate (Public Key) - (idp.institucija.ac.rs.crt) u /etc/ssl/certs
- HTTPS Server Key (Private Key) - (idp.institucija.ac.rs.key) u /etc/ssl/private
Jedna od mogućnosti kako se to može uraditi:
Preuzme se fajl SCSreq.cnf na lokaciju /etc/ssl/private/SCSreq.cnf
Generisati privatni ključ (.key) i zahtev (.csr):
openssl req -new -sha256 -config /etc/ssl/private/SCSreq.cnf -utf8 -keyout /etc/ssl/private/$(hostname -f).key -out /etc/ssl/private/$(hostname -f).csr
Primer postupka kreiranja privatnog ključa i zahteva (koristitli biste drugačiji naziv sertifikata i uneli biste odgovarajuće podatke):
openssl req -new -sha256 -config /etc/ssl/private/SCSreq.cnf -utf8 -keyout /etc/ssl/private/$(hostname -f).key -out /etc/ssl/private/$(hostname -f).csr
Generating a 2048 bit RSA private key
....................+++
....................+++
writing new private key to '/etc/ssl/private/idp.institucija.ac.rs.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Oznaka zemlje (2 znaka) [RS]: Klik Enter
Pun naziv drzave []: Klik Enter
Lokacija (mesto) []: Belgrade
Postanski broj []: 11000
Ulica i broj []: Bulevar kralja Aleksandra 90
Zvanični naziv institucije []: Academic network of the Republic of Serbia – AMRES
FQDN adresa servera []: idp.institucija.ac.rs
Zatim generisani zahtev iskorititi za kreiranje sertifikata (javnog ključa) koji treba da bude tipa GÉANT OV SSL
Preuzimanje CA Cert (GEANT_OV_RSA_CA_4.crt) sertifikata:
wget https://docs.amres.ac.rs/download/shibboleth/GEANT_OV_RSA_CA_4.crt -O /etc/ssl/certs/GEANT_OV_RSA_CA_4.crt
Dati odgovarajuće privilegije SSL sertifikatu i ključu:
Omogućiti Apache2 modul:
Zatim treba restartovati Apache proces:
Ukoliko se prikaže greška proverite:
- Da li ste kreirali privatni ključ i sertifikat i uneli ga na pravilnu lokaciju?
- Da li ste preuzeli GEANT_OV_RSA_CA_4.crt sertifikat?
- Da li ste uneli sve potrebne izmene u okviru fajla /etc/apache2/sites-available/$(hostname -f).conf?
- Da li ste omogućili Apache2 modul prema uputstvu?
- Da li ste instalirali sav potreban softver prema uputstvu (ca-certificates openssl apache2)?
Proveriti IdP metapodatke, koji su dostupni na linku u formi: https://DOMEN_VM/idp/shibboleth
Konfiguracija skladišta Davaoca Identiteta¶
Koriščen je princip: HTML lokalno skladište, GCM enkripcija, bez baze podataka i nije potrebno ništa dodatno konfigurisati.
Proveriti status Davaoca Identiteta:
### Operating Environment Information
### Identity Provider Information
idp_version: 4.3.1
start_time: 2022-08-16T08:51:46.669Z
current_time: 2022-08-16T09:06:12.698285Z
uptime: PT14M26.029S
enabled modules:
idp.authn.Password (Password Authentication)
idp.admin.Hello (Hello World)
installed plugins:
service: shibboleth.LoggingService
last successful reload attempt: 2022-08-16T08:51:41.721516Z
last reload attempt: 2022-08-16T08:51:41.721516Z
service: shibboleth.AttributeFilterService
last successful reload attempt: 2022-08-16T08:51:44.917526Z
last reload attempt: 2022-08-16T08:51:44.917526Z
service: shibboleth.AttributeResolverService
last successful reload attempt: 2022-08-16T08:51:45.016525Z
last reload attempt: 2022-08-16T08:51:45.016525Z
No Data Connector has ever failed
service: shibboleth.AttributeRegistryService
last successful reload attempt: 2022-08-16T08:51:44.392207Z
last reload attempt: 2022-08-16T08:51:44.392207Z
service: shibboleth.NameIdentifierGenerationService
last successful reload attempt: 2022-08-16T08:51:45.144306Z
last reload attempt: 2022-08-16T08:51:45.144306Z
service: shibboleth.RelyingPartyResolverService
last successful reload attempt: 2022-08-16T08:51:45.226265Z
last reload attempt: 2022-08-16T08:51:45.226265Z
service: shibboleth.MetadataResolverService
last successful reload attempt: 2022-08-16T08:51:44.691261Z
last reload attempt: 2022-08-16T08:51:44.691261Z
No Metadata Resolver has ever attempted a reload
service: shibboleth.ReloadableAccessControlService
last successful reload attempt: 2022-08-16T08:51:45.689784Z
last reload attempt: 2022-08-16T08:51:45.689784Z
service: shibboleth.ReloadableCASServiceRegistry
last successful reload attempt: 2022-08-16T08:51:45.736877Z
last reload attempt: 2022-08-16T08:51:45.736877Z
service: shibboleth.ManagedBeanService
last successful reload attempt: 2022-08-16T08:51:45.752055Z
last reload attempt: 2022-08-16T08:51:45.752055Z
Integracija sa OpenLDAP bazom podataka¶
Instalirati ldap-utils paket:
Kreirati sistemski nalog (nalog za monitoring) u OpenLDAP bazi
O tome možete da pročitate u ovom delu uputstva Instalacije i konfiguracije OpenLDAP baze podataka (Debian/Ubuntu) ili ovde (CentOS).
Nakon što kreirate sistemski nalog potrebno je da mu se daju privilegije čitanja (monitoringa) korisničkih naloga u bazi, što se postiže sastavljanjem liste za kontrolu pristupa o čemu možete da pročitate više u ovom delu (Debian/Ubuntu) ili pročitati deo (CentOS) .
Napomena: Ukoliko vam je potrebna konsultacija oko specifičnije liste za kontrolu pristupa kontaktirajte nas na imejl adresu helpdesk@amres.ac.rs.
OpenLDAP sertifikat
Ukoliko se OpenLDAP baza ne nalazi na VM na kojoj se instalira i konfiguriše Shibboleth IdP potrebno je preneti sertifikat baze na ovu VM jer će biti neophodan za ostvarivanje sigurne konekcije sa bazom podataka. Sertifikat se može preneti na lokaciju /etc/ldap/ ili /etc/ldap/certs ili neku vama pogodnu lokaciju. Podatak o lokaciji ovog sertifikata treba da se unese kasnije u fajl /opt/shibboleth-idp/conf/ldap.properties.
Koristi se metoda OpenLDAP + STARTTLS.
Fajl secrets.properties¶
Fajl secrets.properties
U fajlu secrets.properties je sadržana šifra koja je uneta u procesu instalacije Shibboleth Davaoca Identiteta (idp.sealer.storePassword i idp.sealer.keyPassword).
Izmena fajla secrets.properties :
Potrebno je editovati liniju:
- Umesto dela myServicePassword unosi lozinka sistemskog naloga koji će povezati IdP sa LDAP bazom podataka i na taj način omogučiti autentifikaciju korisnika iz baze:
Fajl ldap.properties¶
wget https://docs.amres.ac.rs/download/shibboleth/debian/ldap.properties -O /opt/shibboleth-idp/conf/ldap.properties
U fajl ldap.properties se navode pojedinosti vezane za LDAP bazu sa kojom se IdP povezuje:
idp.authn.LDAP.ldapURL = ldap://<DOMEN VM NA KOJOJ_JE LDAP BAZA> npr. ldap://ldap.institucija.ac.rs
idp.authn.LDAP.trustCertificates = <PUTANJA_DO_LDAP_SERTIFIKATA> npr. /etc/ldap/ldap.institucija.ac.rs.crt
idp.authn.LDAP.baseDN = <DEO LDAP BAZE GDE SU KORISNIČKI NALOZI KOJI SE AUTENTIFIKUJU> npr. ou=people,dc=institucija,dc=ac,dc=rs
idp.authn.LDAP.subtreeSearch = false
idp.authn.LDAP.bindDN = <DN SISTEMSKOG NALOGA> npr. cn=idpuser,ou=system,dc=institucija,dc=ac,dc=rs
idp.attribute.resolver.LDAP.exportAttributes = <ATRIBUTI KOJI SE UZIMAJU IZ LDAP BAZE> npr. uid cn givenName sn mail rsEduPersonAffiliation displayName eduPersonEntitlement rsEduPersonLocalNumber Napomena:
- U primeru iznad vrednost parametra idp.authn.LDAP.baseDN je navedena organizaciona jedinica u kojoj se nalaze svi korisnički nalozi koji se autentifikuju. Ukoliko je Vaša baza podataka kreirana tako da su nalozi organizovani u više grana i organizacionih jedinica, vrednost parametra idp.authn.LDAP.baseDN treba da bude koren LDAP stabla, a vrednost parametra idp.authn.LDAP.subtreeSearch treba da bude true
- eduPersonEntitlement je specijalna vrsta atributa koji se koristi za autorizaciju. Može se koristiti da bi se utvrdilo da li korisnik ima pravo da koristi određeni servis.
- rsEduPersonAffiliation atribut definiše način na koji je osoba povezana sa institucijom (moguće vrednosti su: student, učenik, nastavni kadar, zaposleni, spoljni saradnik, korisnik usluge, gost).
- rsEduPersonLocalNumber atribut predstavlja lokalni identifikator osobe, npr. za studenta broj studenta ili za zaposlenog broj zaposlenog.
Primer popunjenog fajla ldap.properties:
Provera konektivnosti sa LDAP bazom
ldapsearch -x -h <FQDN ili IP adresa> -D '<DN_SISTEMSKOG_NALOGA>' -w '<IDPUSER_PASSWORD>' -b 'ou=people,dc=example,dc=org' '(uid=<KORISNIČKO_IME>)'
<FQDN ili IP adresa> zameniti podatkom o domenu (FQDN) ili IP adresi virtuelne mašine na kojoj je LDAP baza
<DN_SISTEMSKOG_NALOGA> zameniti podatkom o kreiranom sistemskom nalogu npr. cn=idpuser,ou=system,dc=institucija,dc=ac,dc=rs
<IDPUSER_PASSWORD> zameniti lozinkom sistemskog naloga
ou=people,dc=example,dc=org zameniti podatkom o delu LDAP baze gde su korisnički nalozi koji se autentifikuju npr. ou=people,dc=institucija,dc=ac,dc=rs
<KORISNIČKO_IME> zameniti podatkom o korisničkom imenu test naloga za kog se proverava uspešnost autentifikacije Primer komande:
Napomena: Iz komande izbaciti "-h ldap.institucija.ac.rs" parametar ukoliko komanda ne radi, a razlog je što nije podržan na novijoj verzija OS.Restartovati Jetty proces:
Proveriti status Davaoca Identiteta. Napomena: Ukoliko je izveštaj isti kao prethodni put sa konfiguracijom je sve u redu:
Podesiti da Davaoc Identiteta pušta persistent NameID¶
Shibboleth Documentation: https://wiki.shibboleth.net/confluence/display/IDP4/PersistentNameIDGenerationConfiguration
persistent NameID je jedinstveni trajni identifikator korisnika, koji Davalac Identiteta prosleđuje Davaocu Servisa.
Strategija A "Computed mode" (preporučena):¶
mv /opt/shibboleth-idp/conf/saml-nameid.properties /opt/shibboleth-idp/conf/saml-nameid.properties_default
wget https://docs.amres.ac.rs/download/shibboleth/saml-nameid.properties -O /opt/shibboleth-idp/conf/saml-nameid.properties
wget https://docs.amres.ac.rs/download/shibboleth/saml-nameid.xml -O /opt/shibboleth-idp/conf/saml-nameid.xml
Rezultat komande je potrebno sačuvati/kopirati, jer se primenjuje u sledećem koraku
Rezultat komande je niz karaktera formata:
4Z4VL1gOzw*******************************
- Otkomentarisati liniju:
- Deo changethistosomethingrandom izmeniti dobijenim nizom karaktera dobijenim kao rezultat prethodno primenjene komande (openssl rand -base64 36).
Restartovati Jetty proces:
Proveriti status Davaoca Identiteta:
Strategija B "Stored mode" (korišćenje baze podataka za skladištenje persistent NameID)¶
Instalirati potrebne pakete:
Pokrenuti bazu:Pokrenuti proces uspostavljanja bezbedonosne politike MariaDB baze podataka (ukoliko već nije uspostavljena):
Pokretanjem ove komande ulazi se u interaktivni mod, u okviru koga je potrebno odgovotiri na sledeća pitanja:
Kreirati shibpid tabelu u shibboleth bazi podataka:
Potrebno je editovati ###SHIB-USERNAME-CHANGEME### i ###SHIB-DB-USER-PASSWORD-CHANGEME### delove konfiguracije, čime ćete kreirati korisnika koji će biti korišćen kasnije.
Importovati bazu:
Restartovati MariaDB servis: Pokrenuti build skripte za dodavanje neophodnih biblioteka: Omogućiti konekciju sa bazom izmenom sledećeg fajla: Dodati deo konfiguracije pre poslednjeg taga:U delu ###SHIB-USERNAME-CHANGEME### i ###SHIB-DB-USER-PASSWORD-CHANGEME### unesite kredencijale prethodno kreiranog korisnika.
Omogućite kreiranje persistent-id vrednosti preuzimanjem konfiguracionog fajla:
mv /opt/shibboleth-idp/conf/saml-nameid.properties /opt/shibboleth-idp/conf/saml-nameid.properties_default
wget https://docs.amres.ac.rs/download/shibboleth/debian/saml-nameid.properties -O /opt/shibboleth-idp/conf/saml-nameid.properties
wget https://docs.amres.ac.rs/download/shibboleth/debian/saml-nameid.xml -O /opt/shibboleth-idp/conf/saml-nameid.xml
Rezultat komande je potrebno sačuvati/kopirati, jer se primenjuje u sledećem koraku
Rezultat komande je niz karaktera formata:
4Z4VL1gOzw*******************************
- Otkomentarisati liniju:
- Deo changethistosomethingrandom izmeniti dobijenim nizom karaktera dobijenim kao rezultat prethodno primenjene komande (openssl rand -base64 36).
mv /opt/shibboleth-idp/conf/c14n/subject-c14n.xml /opt/shibboleth-idp/conf/c14n/subject-c14n.xml_default
wget https://docs.amres.ac.rs/download/shibboleth/debian/subject-c14n.xml -O /opt/shibboleth-idp/conf/c14n/subject-c14n.xml
mv /opt/shibboleth-idp/conf/c14n/subject-c14n.properties /opt/shibboleth-idp/conf/c14n/subject-c14n.properties_default
wget https://docs.amres.ac.rs/download/shibboleth/debian/subject-c14n.properties -O /opt/shibboleth-idp/conf/c14n/subject-c14n.properties
Restartovati Jetty proces:
Proveriti status Davaoca Identiteta:
Podešavanje attribute-resolver.xml fajla¶
Preuzeti fajl attribute-resolver.xml
mv /opt/shibboleth-idp/conf/attribute-resolver.xml /opt/shibboleth-idp/conf/attribute-resolver_default.xml
U slučaju da ste odabrali Strategiju A "Computed mode" (preporučena) za persistent NameID, preuzimate sledeći fajl:
U slučaju da ste odabrali Strategiju B "Stored mode" za persistent NameID, preuzimate sledeći fajl:
U fajlu treba izmeniti sledeće:
Umesto dela Naziv Vaše institucije uneti naziv Vaše institucije.
Ukoliko želite da učestvujete u Erazmus+ projektu i imate HEI ulogu, potrebno je da dodate konfiguraciju za ESI atribut.
Promeniti vlasnika fajla:
Restartovati Jetty proces:
Proveriti status Davaoca Identiteta:
Podesiti da Shibboleth Identity Provider pušta eduPersonTargetedID¶
Trajni identifikator korisnika koji razmenjuju Davalac Servisa i Davalac Identiteta (Shibboleth IdP). Nikada se ne dodeljuje ponovo i ne sadrži nikakve podatke o korisniku. Davalac Identiteta smešta persistentId vrednost u eduPersonTargetedID atribut kada komunicira sa određenim Davaocem Servisa ukoliko on to zahteva.
Ovaj deo je već podešen u okviru fajla attribute-resolver.xml koji ste preuzeli i izmenili u prethodnim koracima.
Dodatno, potrebno je preuzeti fajl eduPersonTargetedID.properties.
wget https://docs.amres.ac.rs/download/shibboleth/eduPersonTargetedID.properties -O /opt/shibboleth-idp/conf/attributes/custom/eduPersonTargetedID.properties ; chown jetty:root /opt/shibboleth-idp/conf/attributes/custom/eduPersonTargetedID.properties
Restartovati Jetty proces:
Proveriti status Davaoca Identiteta:
Uneti dodatne šeme za definisanje atributa¶
rm /opt/shibboleth-idp/conf/attributes/eduPerson.xml ; wget https://docs.amres.ac.rs/download/shibboleth/eduPerson.xml -O /opt/shibboleth-idp/conf/attributes/eduPerson.xml
rm /opt/shibboleth-idp/conf/attributes/inetOrgPerson.xml ; wget https://docs.amres.ac.rs/download/shibboleth/inetOrgPerson.xml -O /opt/shibboleth-idp/conf/attributes/inetOrgPerson.xml
rm /opt/shibboleth-idp/conf/attributes/samlSubject.xml ; wget https://docs.amres.ac.rs/download/shibboleth/samlSubject.xml -O /opt/shibboleth-idp/conf/attributes/samlSubject.xml
Preuzeti rsEdu.xml i schac.xml šemu na lokaciju /opt/shibboleth-idp/conf/attributes/
wget https://docs.amres.ac.rs/download/shibboleth/rsEdu.xml -O /opt/shibboleth-idp/conf/attributes/rsEdu.xml ; chown jetty:root /opt/shibboleth-idp/conf/attributes/rsEdu.xml
wget https://docs.amres.ac.rs/download/shibboleth/schac.xml -O /opt/shibboleth-idp/conf/attributes/schac.xml ; chown jetty:root /opt/shibboleth-idp/conf/attributes/schac.xml
Preuzeti fajl default-rules.xml :
mv /opt/shibboleth-idp/conf/attributes/default-rules.xml /opt/shibboleth-idp/conf/attributes/default-rules_default.xml
wget https://docs.amres.ac.rs/download/shibboleth/default-rules.xml -O /opt/shibboleth-idp/conf/attributes/default-rules.xml
Konfiguracija Shibboleth IdP Logova¶
Konfiguracija logova vezanih za LDAP greške u autentifikaciji:
wget https://docs.amres.ac.rs/download/shibboleth/logback.xml -O /opt/shibboleth-idp/conf/logback.xml
Podešavanje interfejsa¶
Preuzeti korisnički interfejs na lokaciju /opt/shibboleth-idp/:
wget https://docs.amres.ac.rs/download/shibboleth/4.3.1/edit-webapp.tar.gz -O /opt/shibboleth-idp/edit-webapp.tar.gz ; rm -Ir /opt/shibboleth-idp/edit-webapp
Uneti logo vaše institucije u direktorijum: /opt/shibboleth-idp/edit-webapp/images
- Imate mogućnost da unesete 2 logo fajla, jedan na srpskom i engleskom i shodno tome treba dati naziv formata npr. institucija_logo_sr.jpg i institucija_logo_en.jpg
- Dimenzije: širina do 200px.
- Podatak o logou institucije treba uneti u kasnijim koracima u fajlove messages_sr.properties i messages_en.properties
Prevod interfejsa i sistemskih poruka se preuzima u direktorijum /opt/shibboleth-idp/messages
wget https://docs.amres.ac.rs/download/shibboleth/messages_sr.properties -O /opt/shibboleth-idp/messages/messages_sr.properties
Izmeniti parametre:
- idp.title=Institucija Web SSO
- idp.logo=/images/institucija_logo_sr.jpg
- idp.userprefs.title=Institucija Web SSO
wget https://docs.amres.ac.rs/download/shibboleth/messages_en.properties -O /opt/shibboleth-idp/messages/messages_en.properties
Izmeniti parametar:
- idp.logo=/images/institucija_logo_en.jpg
U okviru fajla /opt/shibboleth-idp/messages/messages.properties izmeniti parametre:
- idp.css = /css/amres.css
- idp.logo=/images/institucija_logo_sr.jpg
Sledi prikaz pozicije i okvirnih dimenzija logo fotografije, kao primer je prikazan logo institucije AMRES.

Ilustracija logo fotografije za IdP
Preimenovanje postojećih i preuzimanje novih fajlova user-prefs.vm, logout-propagate.vm, logout-complete.vm, error.vm, login.vm i logout.vm
mv /opt/shibboleth-idp/views/user-prefs.vm /opt/shibboleth-idp/views/user-prefs_default.vm ; wget https://docs.amres.ac.rs/download/shibboleth/4.3.1/user-prefs.vm -O /opt/shibboleth-idp/views/user-prefs.vm
mv /opt/shibboleth-idp/views/logout-propagate.vm /opt/shibboleth-idp/views/logout-propagate_default.vm ; wget https://docs.amres.ac.rs/download/shibboleth/4.3.1/logout-propagate.vm -O /opt/shibboleth-idp/views/logout-propagate.vm
mv /opt/shibboleth-idp/views/logout-complete.vm /opt/shibboleth-idp/views/logout-complete_default.vm ; wget https://docs.amres.ac.rs/download/shibboleth/4.3.1/logout-complete.vm -O /opt/shibboleth-idp/views/logout-complete.vm
mv /opt/shibboleth-idp/views/error.vm /opt/shibboleth-idp/views/error_default.vm ; wget https://docs.amres.ac.rs/download/shibboleth/4.3.1/error.vm -O /opt/shibboleth-idp/views/error.vm
mv /opt/shibboleth-idp/views/login.vm /opt/shibboleth-idp/views/login_default.vm ; wget https://docs.amres.ac.rs/download/shibboleth/4.3.1/login.vm -O /opt/shibboleth-idp/views/login.vm
mv /opt/shibboleth-idp/views/logout.vm /opt/shibboleth-idp/views/logout_default.vm ; wget https://docs.amres.ac.rs/download/shibboleth/4.3.1/logout.vm -O /opt/shibboleth-idp/views/logout.vm
mv /opt/shibboleth-idp/views/login-error.vm /opt/shibboleth-idp/views/login-error_default.vm ; wget https://docs.amres.ac.rs/download/shibboleth/4.3.1/login-error.vm -O /opt/shibboleth-idp/views/login-error.vm
mv /opt/shibboleth-idp/views/admin/hello.vm /opt/shibboleth-idp/views/admin/hello_default.vm ; wget https://docs.amres.ac.rs/download/shibboleth/4.3.1/hello.vm -O /opt/shibboleth-idp/views/admin/hello.vm
mv /opt/shibboleth-idp/views/client-storage/client-storage-read.vm /opt/shibboleth-idp/views/client-storage/client-storage-read_default.vm ; wget https://docs.amres.ac.rs/download/shibboleth/4.3.1/client-storage-read.vm -O /opt/shibboleth-idp/views/client-storage/client-storage-read.vm
mv /opt/shibboleth-idp/views/client-storage/client-storage-write.vm /opt/shibboleth-idp/views/client-storage/client-storage-write_default.vm ; wget https://docs.amres.ac.rs/download/shibboleth/4.3.1/client-storage-write.vm -O /opt/shibboleth-idp/views/client-storage/client-storage-write.vm
Restartovati Jetty servis:
Izveštaj pokretanja skripte
Buildfile: /opt/shibboleth-idp/bin/build.xml
build-war:
Installation Directory: [/opt/shibboleth-idp] ? Klik ENTER
INFO - Including auto-located properties in /opt/shibboleth-idp/conf/c14n/subject-c14n.properties
INFO - Including auto-located properties in /opt/shibboleth-idp/conf/services.properties
INFO - Including auto-located properties in /opt/shibboleth-idp/conf/authn/authn.properties
INFO - Including auto-located properties in /opt/shibboleth-idp/conf/saml-nameid.properties
INFO - Including auto-located properties in /opt/shibboleth-idp/conf/ldap.properties
INFO - Including auto-located properties in /opt/shibboleth-idp/conf/admin/admin.properties
Rebuilding /opt/shibboleth-idp/war/idp.war, Version 4.3.1
Initial populate from /opt/shibboleth-idp/dist/webapp to /opt/shibboleth-idp/webpapp.tmp
Overlay from /opt/shibboleth-idp/edit-webapp to /opt/shibboleth-idp/webpapp.tmp
Creating war file /opt/shibboleth-idp/war/idp.war
BUILD SUCCESSFUL
Total time: 5 seconds
Restartovati Jetty servis:
Izmeniti fajl idp-metadata.xml¶
Pre bilo koje izmene ovog fajla najsigurnije je napraviti njegovu kopiju
Ovaj fajl je veoma značajan i unikatan. Iz tog razloga treba vrlo pažljivo izvršiti sve potrebne izmene i u slučaju potrebe zgodno je imati mogućnost povratka na početno stanje.
Domen (npr. idp.institucija.ac.rs) u ovom fajlu nije potrebno menjati, već je podešen na osnovu definicija iz prethodnih fajlova.
Obrisati kompletno sledeći komentar:
Obrisati deo validUntil="2022-01-30T18:18:24.695Z" u sledećoj celini. Napomena: Vama će biti generisan drugačiji datum i vreme:
<EntityDescriptor xmlns="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" xmlns:shibmd="urn:mace:shibboleth:metadata:1.0" xmlns:xml="http://www.w3.org/XML/1998/namespace" xmlns:mdui="urn:oasis:names:tc:SAML:metadata:ui" xmlns:req-attr="urn:oasis:names:tc:SAML:protocol:ext:req-attr" validUntil="2022-02-07T21:13:49.962Z" entityID="https://idp.institucija.amres.ac.rs/idp/shibboleth">
<EntityDescriptor xmlns="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" xmlns:shibmd="urn:mace:shibboleth:metadata:1.0" xmlns:xml="http://www.w3.org/XML/1998/namespace" xmlns:mdui="urn:oasis:names:tc:SAML:metadata:ui" xmlns:req-attr="urn:oasis:names:tc:SAML:protocol:ext:req-attr" entityID="https://idp.institucija.amres.ac.rs/idp/shibboleth">
Obrisati deo:
<!--
Fill in the details for your IdP here
<mdui:UIInfo>
<mdui:DisplayName xml:lang="en">A Name for the IdP at idp.institucija.amres.ac.rs</mdui:DisplayName>
<mdui:Description xml:lang="en">Enter a description of your IdP at idp.institucija.amres.ac.rs</mdui:Description>
<mdui:Logo height="80" width="80">https://idp.institucija.ac.rs/Path/To/Logo.png</mdui:Logo>
</mdui:UIInfo>
-->
Umesto tog dela dodati sledeći deo uz određene izmene:
Izmeniti sledeće podatke:
- Naziv institucije: Uneti pun naziv institucije.
- Name of the Institution: Uneti pun naziv institucije na engleskom jeziku.
- IDP za zaposlene u instituciji: Svrha korišćenja IdP-a, npr. IDP za zaposlene u instituciji.
- IDP for staff in the Institution: Svrha korišćenja IdP-a na engleskom jeziku , npr. IDP for staff in the Institution.
- https://amres.ac.rs/dokumenti/amres_idp.png : Logo fotografija dostupna putem linka koji se navodi, širine i visine 50px.
Sledi prikaz pozicije i okvirnih dimenzija logo fotografije, kao primer je dat logo institucije AMRES. Ova logo fotografija bi se prikazala prilikom odabira Vaše institucije (Davaoca Identiteta) prilikom autentifikacije na željeni servis.
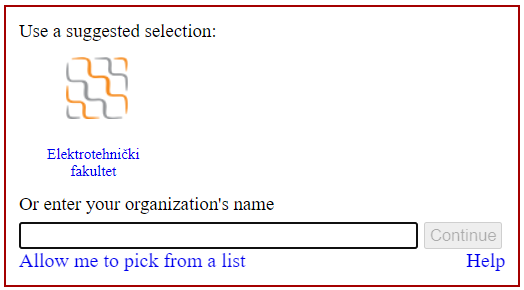
Ilustracija logo fotografije za IdP, koja se unosi putem linka
Obrisati deo
Sledeći korak:
U sledećoj celini potrebno je obrisati niz karaktera :8443 i izmeniti da indeks bude 1 umesto 2:
Sledeći korak:
Obrisati oznake za komentar dela SingleLogoutService:
<!--
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://idp.institucija.ac.rs/idp/profile/SAML2/POST/SLO"/>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://idp.institucija.ac.rs:8443/idp/profile/SAML2/SOAP/SLO"/>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://idp.institucija.ac.rs/idp/profile/SAML2/Redirect/SLO"/>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-SimpleSign" Location="https://idp.institucija.ac.rs/idp/profile/SAML2/POST-SimpleSign/SLO"/>
-->
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://idp.institucija.ac.rs/idp/profile/SAML2/POST/SLO"/>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://idp.institucija.ac.rs:8443/idp/profile/SAML2/SOAP/SLO"/>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://idp.institucija.ac.rs/idp/profile/SAML2/Redirect/SLO"/>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-SimpleSign" Location="https://idp.institucija.ac.rs/idp/profile/SAML2/POST-SimpleSign/SLO"/>
Sledeći korak:
U sledećoj celini potrebno je obrisati niz kataktera :8443
Sledeći korak:
Obrisati deo
Sledeći korak:
Dodati sledeće 2 linije između poslednje SingleLogoutService Binding i prve SingleSignOnService Binding sekcije:
...
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-SimpleSign" Location="https://idp.institucija.ac.rs/idp/profile/SAML2/POST-SimpleSign/SLO"/>
<NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:transient</NameIDFormat>
<NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:persistent</NameIDFormat>
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" req-attr:supportsRequestedAttributes="true" Location="https://idp.institucija.ac.rs/idp/profile/SAML2/Redirect/SSO"/>
...
Sledeći korak:
Sledeći korak:
Sledeći korak:
Obrisati dve oznake za komentar na početku i kraju reda (kraj prethodnog komentara i početak narednog) u sledećoj liniji:
Napomena: Ostaviti komentar u sredini
Sledeći korak:
Obrisati sve oznake za komentar u delu:
Sledeći korak:
U sledećem delu potrebno je obrisati niz karaktera :8443
Obrisati u potpunosti delove:
Sledeći korak:
Ispod linije </AttributeAuthorityDescriptor> a iznad linije </EntityDescriptor> dodati sledeću sekciju:
Izmeniti sledeće podatke:
- Naziv institucije: Pun naziv Vaše institucije
- Name of the Institution: Pun naziv Vaše institucije na engleskom jeziku
- Naziv (akronim) institucije: Akronim Vaše institucije
- Naziv (akronim) institucije: Akronim Vaše institucije na engleskom
- https://institucija.ac.rs/: Link do verzije sajta institucije na srpskom jeziku
- https://institucija.ac.rs/en: Link do verzije sajta institucije na engleskom jeziku
- Ime: Ime osobe za kontakt
- Prezime: Prezime osobe za kontakt
- primer@institucija.ac.rs: Imejl adresa osobe za kontak
Fajl idp-metadata.xml nakon svih navedenih izmena:
<?xml version="1.0" encoding="UTF-8"?>
<EntityDescriptor xmlns="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" xmlns:shibmd="urn:mace:shibboleth:metadata:1.0" xmlns:xml="http://www.w3.org/XML/1998/namespace" xmlns:mdui="urn:oasis:names:tc:SAML:metadata:ui" xmlns:req-attr="urn:oasis:names:tc:SAML:protocol:ext:req-attr" entityID="https://idp.institucija.amres.ac.rs/idp/shibboleth">
<IDPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<Extensions>
<shibmd:Scope regexp="false">institucija.ac.rs</shibmd:Scope>
<mdui:UIInfo>
<mdui:DisplayName xml:lang="sr">Institucije Republike Srbije</mdui:DisplayName>
<mdui:DisplayName xml:lang="en">Institutions of the Republic of Serbia</mdui:DisplayName>
<mdui:Description xml:lang="sr">IDP za zaposlene u Institucijama Republike Srbije</mdui:Description>
<mdui:Description xml:lang="en">IDP for staff in the Institutions of the Republic of Serbia </mdui:Description>
<mdui:Logo height="200" width="200">https://e7.pngegg.com/pngimages/34/35/png-clipart-flag-of-serbia-flags-of-the-world-flag-of-serbia-flag-logo.png</mdui:Logo>
</mdui:UIInfo>
</Extensions>
<!-- First signing certificate is BackChannel, the Second is FrontChannel-->
<KeyDescriptor use="signing">
<ds:KeyInfo>
<ds:X509Data>
<ds:X509Certificate>
...
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</KeyDescriptor>
<KeyDescriptor use="signing">
<ds:KeyInfo>
<ds:X509Data>
<ds:X509Certificate>
...
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</KeyDescriptor>
<KeyDescriptor use="encryption">
<ds:KeyInfo>
<ds:X509Data>
<ds:X509Certificate>
...
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</KeyDescriptor>
<ArtifactResolutionService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://idp.institucija.ac.rs/idp/profile/SAML2/SOAP/ArtifactResolution" index="1"/>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-SimpleSign" Location="https://idp.institucija.ac.rs/idp/profile/SAML2/POST-SimpleSign/SLO"/>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://idp.institucija.ac.rs/idp/profile/SAML2/SOAP/SLO"/>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://idp.institucija.ac.rs/idp/profile/SAML2/Redirect/SLO"/>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://idp.institucija.ac.rs/idp/profile/SAML2/POST/SLO"/>
<NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:transient</NameIDFormat>
<NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:persistent</NameIDFormat>
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-SimpleSign" req-attr:supportsRequestedAttributes="true" Location="https://idp.institucija.ac.rs/idp/profile/SAML2/POST-SimpleSign/SSO"/>
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" req-attr:supportsRequestedAttributes="true" Location="https://idp.institucija.ac.rs/idp/profile/SAML2/Redirect/SSO"/>
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" req-attr:supportsRequestedAttributes="true" Location="https://idp.institucija.ac.rs/idp/profile/SAML2/POST/SSO"/>
</IDPSSODescriptor>
<AttributeAuthorityDescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<Extensions>
<shibmd:Scope regexp="false">institucija.ac.rs</shibmd:Scope>
</Extensions>
<!-- First signing certificate is BackChannel, the Second is FrontChannel-->
<KeyDescriptor use="signing">
<ds:KeyInfo>
<ds:X509Data>
<ds:X509Certificate>
...
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</KeyDescriptor>
<KeyDescriptor use="signing">
<ds:KeyInfo>
<ds:X509Data>
<ds:X509Certificate>
...
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</KeyDescriptor>
<KeyDescriptor use="encryption">
<ds:KeyInfo>
<ds:X509Data>
<ds:X509Certificate>
...
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</KeyDescriptor>
<AttributeService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://idp.institucija.ac.rs/idp/profile/SAML2/SOAP/AttributeQuery"/>
</AttributeAuthorityDescriptor>
<Organization>
<OrganizationName xml:lang="sr">Naziv institucije</OrganizationName>
<OrganizationName xml:lang="en">Name of the Institution</OrganizationName>
<OrganizationDisplayName xml:lang="sr">Naziv (akronim) institucije</OrganizationDisplayName>
<OrganizationDisplayName xml:lang="en">Short name of the Institution</OrganizationDisplayName>
<OrganizationURL xml:lang="sr">https://institucija.ac.rs/</OrganizationURL>
<OrganizationURL xml:lang="en">https://institucija.ac.rs/en</OrganizationURL>
</Organization>
<ContactPerson contactType="technical">
<GivenName>Ime</GivenName>
<SurName>Prezime</SurName>
<EmailAddress>primer@institucija.ac.rs</EmailAddress>
</ContactPerson>
</EntityDescriptor>
Nakon izvršenih izmena metapodaci vašeg Davaoca Identiteta dostupni su na linku https://institucija.ac.rs/idp/shibboleth
Podešavanje kolačića i ostalih podataka¶
Preuzeti skriptu updateIDPsecrets.sh na lokaciju /opt/shibboleth-idp/bin/:
wget https://docs.amres.ac.rs/download/shibboleth/updateIDPsecrets.sh -O /opt/shibboleth-idp/bin/updateIDPsecrets.sh
Toj skripti treba dati potrebnu dozvolu za izvršavanje:
Preuzeti CRON skriptu (/etc/cron.daily/updateIDPsecrets) koja će da je pokreće:
wget https://docs.amres.ac.rs/download/shibboleth/updateIDPsecrets -O /etc/cron.daily/updateIDPsecrets
Toj skripti treba dati potrebnu dozvolu za izvršavanje:
Proveriti da li će se skripta pokretati svakog dana (daily) :
Izveštaj provere:
Konfigurisati IdP da koristi adekvatan Attribute Filter Policy dokument¶
Kreirati direktorijum tmp/httpClientCache
mkdir -p /opt/shibboleth-idp/tmp/httpClientCache ; chown jetty /opt/shibboleth-idp/tmp/httpClientCache
Preuzeti fajl services.xml:
wget https://docs.amres.ac.rs/download/shibboleth/services.xml -O /opt/shibboleth-idp/conf/services.xml
Restartovati Jetty servis:
Proveriti status Davaoca Identiteta:
Pridruživanje iAMRES Federaciji¶
Pridruživanje iAMRES Federaciji podrazumeva razmenu metapodataka konfigurisanog Davaoca Identiteta i postojećih Davalaca Servisa. U narednim koracima potrebno je preuzeti metapodatke Davalaca Servisa iAMRES Federacije.
Preuzeti sertifikate za potpis metapodatka na lokaciju: /opt/shibboleth-idp/metadata/
wget https://docs.amres.ac.rs/download/shibboleth/md.iamres.ac.rs.crt -O /opt/shibboleth-idp/metadata/md.iamres.ac.rs.crt
Preuzeti skriptu za preuzimanje metapodataka SP entiteta iAMRES Federacije (metadata.sh) na lokaciju: /opt/shibboleth-idp/metadata/
wget https://docs.amres.ac.rs/download/shibboleth/metadata.sh -O /opt/shibboleth-idp/metadata/metadata.sh
Dati skripti odgovarajuću privilegiju za izvršavanje:
Pokrenuti skriptu:
Rezultat pokretanja skripte je kreiranje fajla iamres_federacija_metadata.xml
- Ovaj fajl predstavlja skup metapodataka Davaoca Servisa iAMRES Federacije.
Preuzeti fajl metadata-providers.xml na lokaciju /opt/shibboleth-idp/conf/:
wget https://docs.amres.ac.rs/download/shibboleth/metadata-providers.xml -O /opt/shibboleth-idp/conf/metadata-providers.xml
Pregled fajla metadata-providers.xml sa tumačenjem njegovog sadržaja:
- U prikazanom delu fajla navode se Davaoci Servisa iAMRES Federacije, čiji su metapodaci preuzeti skriptom (./metadata.sh) i čitaju se iz gore pomenutog fajla (iamres_federacija_metadata.xml). Ovi metapodaci su potpisani sertifikatom md.iamres.ac.rs.crt.
<MetadataProvider
id="iAMRES"
xsi:type="FilesystemMetadataProvider"
metadataFile="%{idp.home}/metadata/iamres_federacija_metadata.xml">
<MetadataFilter xsi:type="SignatureValidation" requireSignedRoot="true" certificateFile="${idp.home}/metadata/md.iamres.ac.rs.crt"/>
<MetadataFilter xsi:type="RequiredValidUntil" maxValidityInterval="P10D"/>
<MetadataFilter xsi:type="EntityRoleWhiteList">
<RetainedRole>md:SPSSODescriptor</RetainedRole>
</MetadataFilter>
<MetadataFilter xsi:type="Algorithm">
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes128-cbc"/>
<Entity>https://testsp3.amres.ac.rs/simplesaml/module.php/saml/sp/metadata.php/default-sp</Entity>
<Entity>https://ucionica.amres.ac.rs/auth/saml2/sp/metadata.php</Entity>
<Entity>https://proxy.iamres.amres.ac.rs/simplesaml/module.php/saml/sp/metadata.php/amres.ac.rs</Entity>
</MetadataFilter>
</MetadataProvider>
- U prikazanom delu fajla navode se Davaoci Servisa eduGAIN Interfederacije, čiji se metapodaci dinamički preuzimaju sa linka (http://md.iamres.ac.rs/iamres_metadata/iamres-interfederation-sp-metadata.xml). Pored toga kreira se i njihov backingFile (eduGAIN-metadata.xml). Ovi metapodaci su potpisani sertifikatom md.iamres.ac.rs.crt.
<MetadataProvider
id="eduGAIN"
xsi:type="FileBackedHTTPMetadataProvider"
backingFile="%{idp.home}/metadata/eduGAIN-metadata.xml"
metadataURL="http://md.iamres.ac.rs/iamres_metadata/iamres-interfederation-sp-metadata.xml">
<MetadataFilter xsi:type="SignatureValidation" requireSignedRoot="true" certificateFile="${idp.home}/metadata/md.iamres.ac.rs.crt"/>
<MetadataFilter xsi:type="RequiredValidUntil" maxValidityInterval="P10D"/>
<MetadataFilter xsi:type="Algorithm">
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes128-cbc"/>
<!-- <Entity>https://ucionica.amres.ac.rs/auth/saml2/sp/metadata.php</Entity>-->
</MetadataFilter>
</MetadataProvider>
- U prikazanom delu fajla navode se Davaoci Servisa čiji se metapodaci unose ručno u posebnim fajlovima, u okviru direktorijuma /opt/shibboleth-idp/metadata/sourceDirectory/:
<MetadataProvider
id="iAMRESlocalDynamic"
xsi:type="LocalDynamicMetadataProvider"
sourceDirectory="%{idp.home}/metadata/sourceDirectory">
<MetadataFilter xsi:type="Algorithm">
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes128-cbc"/>
<Entity>https://filesender-test.amres.ac.rs/simplesamlphp/module.php/saml/sp/metadata.php/default-sp</Entity>
</MetadataFilter>
</MetadataProvider>
-
Ukoliko budete imali potrebu za ručnim dodavanjem Davaoca Servisa u okviru direktorijuma /opt/shibboleth-idp/metadata/sourceDirectory/ fajlove kreirate tako što je naziv jednog xml fajla SHA-1 heš sažetak entityID vrednosti Davaoca Servisa, na koji je dodata ekstenzija ".xml" i dobija se na sledeći način:
-
Primer generisanja naziva fajla koristeći OpenSSL iz komandne linije i entityID vrednost urn:test:foobar :
Nakon preuzetih fajlova i pokretanja skripte sadržaj direktorijuma /opt/shibboleth-idp/metadata/ je sledeći:
[root@idp metadata]# ll
-rw-rw-r-- 1 jetty jetty 25921531 Aug 4 14:22 eduGAIN-metadata.xml
-rw-r--r-- 1 root root 263457 Aug 4 13:55 iamres_federacija_metadata.xml
-rw-r--r-- 1 root root 15043 Feb 7 23:16 idp-metadata_default.xml
-rw-r--r-- 1 root root 15081 Jul 21 10:56 idp-metadata.xml
-rw-r--r-- 1 root root 1980 Feb 8 10:27 md.iamres.ac.rs.crt
-rwxr-xr-x 1 root root 192 Feb 8 10:27 metadata.sh
drwxrwxr-x 2 jetty jetty 6 Feb 9 11:38 sourceDirectory
Nakon izvršene konfiguracije i preuzimanja metapodataka, potrebno je registrovati metapodatke vašeg Davaoca Identiteta na iAMRES Federaciju, slanjem mejla sa linkom https://institucija.ac.rs/idp/shibboleth na helpdesk@amres.ac.rs.
Crontab:¶
Potrebno je da se podesi da se skripta metadata.sh pokreće na svaki pun sat (u 00) svakog dana:
Uslovi korišćenja i saglasnost za slanje podataka¶
Uvesti Consent modul (modul za davanje saglasnosti):
Rezultat komande
Omogućiti Consent Module preuzimanjem fajla /opt/shibboleth-idp/conf/relying-party.xml
wget https://docs.amres.ac.rs/download/shibboleth/relying-party.xml -O /opt/shibboleth-idp/conf/relying-party.xml
Preuzeti fajl /opt/shibboleth-idp/views/intercept/attribute-release.vm:
mv /opt/shibboleth-idp/views/intercept/attribute-release.vm /opt/shibboleth-idp/views/intercept/attribute-release_default.vm
wget https://docs.amres.ac.rs/download/shibboleth/4.3.1/attribute-release.vm -O /opt/shibboleth-idp/views/intercept/attribute-release.vm
Preuzeti fajl /opt/shibboleth-idp/views/intercept/terms-of-use.vm:
mv /opt/shibboleth-idp/views/intercept/terms-of-use.vm /opt/shibboleth-idp/views/intercept/terms-of-use_default.vm
wget https://docs.amres.ac.rs/download/shibboleth/4.3.1/terms-of-use.vm -O /opt/shibboleth-idp/views/intercept/terms-of-use.vm
Izveštaj pokretanja skripte
Treba enter negde
Restartovati Jetty servis:
Testiranje slanja atributa iz komandne linije¶
Ovu komandu je moguće koristiti nakon pridruživanje iAMRES federaciji, u cilju testiranja slanja atributa ka Test servisu.
Napomena: Umesto
Pregled korisnih logova¶
Jetty logovi:¶
Shibboleth IdP logovi:¶
Audit Log:
Consent Log:
Warn Log:
Process Log: